How Decentralized Digital Identities are Reshaping Future of User-Centric Experiences

4 mins
Last Edited: Nov 29, 2023
Share
How Decentralized Digital Identities are Reshaping Future of User-Centric Experiences
Distributed Digital Identity empower users, enhance data privacy, and revolutionize identity verification. Explore technical details, benefits, real-world applications, and challenges.
Advanced
Decentralised Identities
"In today's digital age, managing and protecting our online identities is more important than ever." However, traditional identity systems are plagued by several problems:
Lack of privacy: Users often have little control over how their personal data is collected, used, and shared by these companies.
Centralized control: Most identity systems are controlled by a small number of companies, creating single points of failure and increasing the risk of data breaches.
Limited interoperability: Different identity systems often don't work well together, making it harder for users to control and manage their online identities across different platforms.
This is where Distributed Identities come in.
Blockchain technology offers a new paradigm for digital identity, with the potential to revolutionize the way we think about identity management. By providing a decentralized, secure, and tamper-proof way to store and share identity data, blockchain technology can help address various challenges associated with traditional identity systems.
Concept of Distributed Digital Identities
Distributed digital identities (DDIs) are closely aligned with the principles of Web3, which advocates for a more decentralized and user-controlled Internet. DDIs represent a shift towards a more user-centric Internet, where users have greater control over their online identities, presence, and privacy.
By leveraging decentralized technologies, DDIs provide a more secure, robust, and flexible approach to online identity management. This paves the way for a more open and inclusive internet that is more resilient and trustworthy than the current web, which is controlled by a few large centralized platforms.
It ultimately reverses the direction of permissioned data sharing — "where instead of users requesting permission from platforms, platforms request permission from users "- recasting the Facebooks and Twitters of the world more as indexers than gatekeepers. This structure enables use cases that would open the door to a new digital identity economy.
How do Distributed Digital Identities Work?
In a decentralized identity system, the following parties interact with the blockchain:
Credential Holder:
The credential holder is an individual or entity that possesses a digital identity stored on a blockchain. This digital identity includes a unique digital identifier (DID) and an associated public key. The use of a blockchain ensures the security and immutability of the stored information, as the data is distributed across a network of nodes.
Issuer:
The issuer is an organization or entity responsible for granting and verifying credentials. This could be a licensing organization, educational institution, or any entity issuing digital credentials. The issuer utilizes its own DID (Digital Identifier) and a private key to sign the credential. By signing the credential with its private key, the issuer adds a cryptographic signature to the information, creating a verifiable link between the credential and the issuing entity. This process ensures the authenticity of the credential, as only the legitimate issuer possesses the private key required to produce a valid signature.
Verifier:
The verifier is a party that needs to confirm the authenticity of a credential presented by the credential holder. The verifier checks the blockchain to validate that the credential was indeed issued by a trusted entity (the issuer). The verification process includes confirming that the credential is associated with the DID of the credential holder who is claiming it. The decentralized and transparent nature of the blockchain allows verifiers to independently and reliably verify the credentials without relying on a central authority.
In summary, this system leverages blockchain technology to ensure the security, authenticity, and decentralized verification of digital credentials. The blockchain serves as a tamper-resistant and transparent ledger that enhances trust in the digital identity ecosystem.
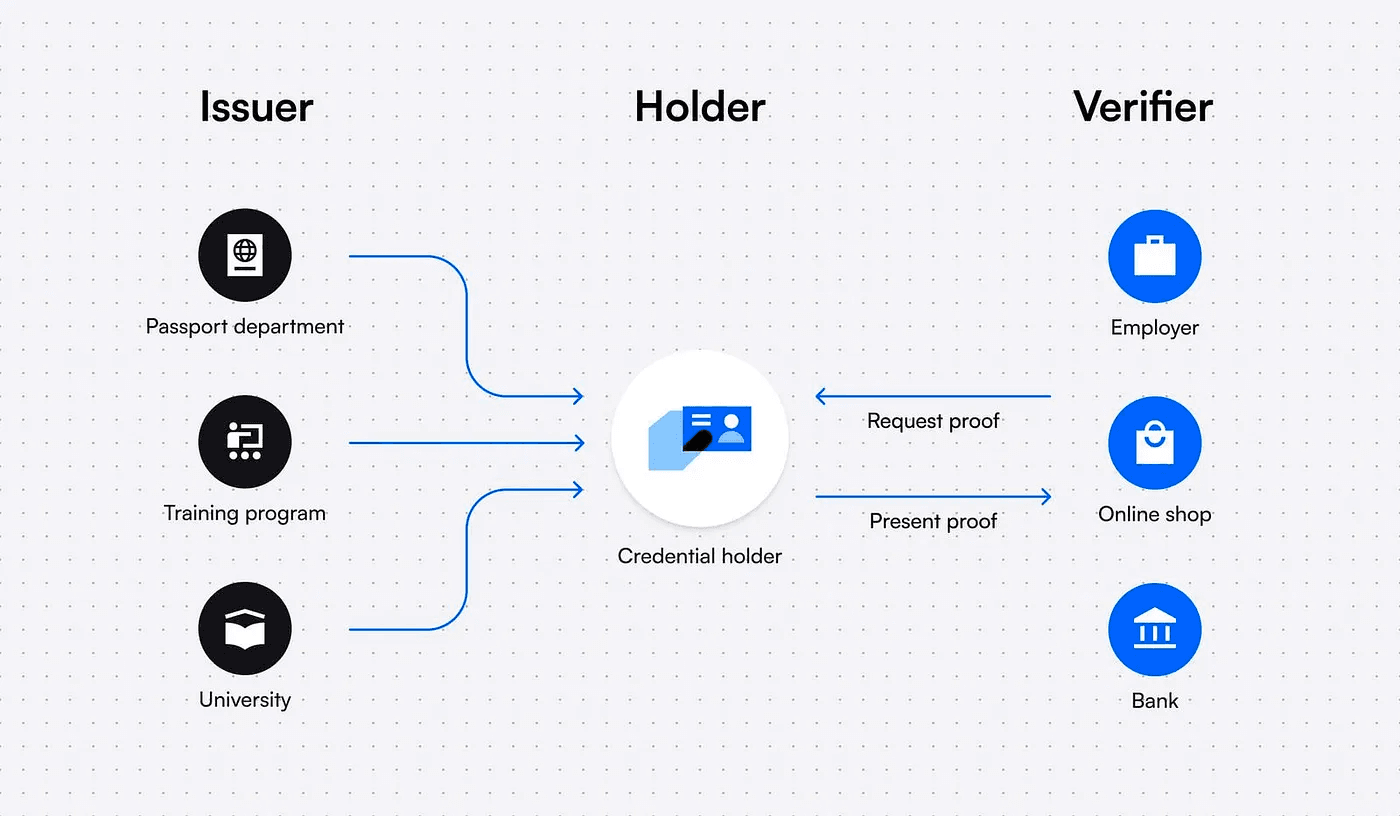
Image source- dock.io
Types of Distributed Digital Identities
There are several different types of distributed identity systems in use today, including:
Self-Sovereign Identity (SSI)
Self-Sovereign Identity (SSI) systems empower individuals to take ownership and control over their personal identity data, eliminating the need for intermediaries like governments or corporations. Users can create multiple "personas" for different online services and choose which data to share with each service. SSI systems typically use decentralized technologies like blockchain to provide security and trust. Example use cases include secure login and authentication, digital wallets, and personal data management.
Example: Veramo, SelfKey, Civic
Decentralized Identity (DID)
The decentralized identity uses blockchain technology to create secure digital identities that are under the user's control. It eliminates the need for a central authority to manage and verify identities, providing greater privacy and security. Users can share only the necessary information with online services without the risk of data breaches. This technology has the potential to revolutionize the way we manage online identities and interactions in the digital world.
Example: Ethereum Name Service (ENS), Sovrin, Blockstack
Federated Identity
Federated identity simplifies the login process by allowing users to use a single set of credentials to access multiple online services. It uses a central identity provider to authenticate users and share their identity data with other services. This makes it easier for users to access various systems and applications while maintaining security and privacy. Federated identity is widely used in enterprise and corporate environments.
Example- Metamask, Brave, Coinbase Wallet.
Verifiable Credentials (VCs)
VCs are digital credentials that can be issued, stored, and verified on a blockchain network. They can represent anything from educational qualifications to professional certifications.
Example- Digital employee identification cards, digital birth certificates, and digital educational certificates.
Benefits of Distributed Digital Identities
The blockchain plays a key role in enabling secure and decentralized identity management in a few ways:
- Immutability: Transactions on a blockchain are recorded in an immutable ledger, making it difficult for any party to alter or delete identity data.
- Decentralization: By distributing data across multiple nodes on a network, blockchain creates a decentralized and tamper-proof system for identity management.
- Smart Contracts: Smart contracts on a blockchain can be used to automate identity verification and validation processes, reducing the need for intermediaries and increasing efficiency.
- Privacy: By encrypting identity data and using zero-knowledge proofs, blockchain can help protect user privacy while still enabling identity verification.
In essence, the blockchain serves as a secure and transparent ledger for verifying the authenticity of digital identities and credentials.
Use Cases of Distributed Digital Identities
Distributed Digital Identity systems could have some pretty transformative effects on the world, here's a few ways:
More Access to Services: Individuals who may not have access to traditional identity documents, like birth certificates or passports, could use a blockchain-based identity to access vital services like healthcare, education, and financial services.
Reduced Fraud and Identity Theft: Distributed identity systems can help reduce the risk of fraud and identity theft, as they make it more difficult for criminals to steal or forge identities.
Increased Privacy: Blockchain-based identity systems give individuals more control over their personal data, which can help protect their privacy and prevent unauthorized access to sensitive information.
Greater Transparency and Accountability: Distributed identity systems can increase accountability and help reduce corruption and unethical behavior by creating a transparent and auditable record of identity-related transactions.
Boosting Financial Inclusion: Distributed identity systems can help provide access to financial services for underbanked and unbanked individuals, particularly in developing countries, by providing a secure, verifiable, and cost-effective means of identity verification. This could lead to greater economic opportunities and more inclusive financial systems.
Revolutionizing Voting Systems: Distributed identity systems can enable secure, transparent, and tamper-proof electronic voting systems that could increase voter turnout, reduce voter fraud, and increase confidence in election results.
Enabling New Forms of Digital Ownership: Distributed identity systems can also enable new forms of digital ownership, such as non-fungible tokens (NFTs) and digital collectibles. This could unlock new forms of economic activity and creativity online.
Adoption Challenges
All is not merry in the world of distributed identities; the challenges of adoption are real, and these include:
Regulatory Hurdles: Governments and regulatory bodies may be hesitant to embrace distributed identity systems due to concerns about cybersecurity, privacy, and compliance with existing regulations.
Technical Challenges: Developing and deploying distributed identity systems can be technically complex and require significant investment in infrastructure and expertise.
User Adoption: Distributed identity systems must be user-friendly and widely accepted by individuals and organizations to succeed. This may require significant education and outreach efforts to overcome skepticism and lack of awareness.
Lack of Interoperability: Different distributed identity systems may not be compatible with each other, creating silos of data that limit the potential for widespread adoption and usage.
User Control and Consent: Ensuring that users have control over their identity data and can give consent for its use can be challenging, particularly in cases where multiple parties need access to the data.
Data Portability: Users should be able to move their identity data between different systems and services easily. However, this requires standardized data formats and protocols that may not yet be widely available.
Conclusion
In the ever-expanding digital world, secure and trustworthy digital identities have become essential. Decentralized identity systems provide a new way to manage digital identities, leveraging the security and transparency of the blockchain to store and verify identities and credentials. These systems offer several benefits, including increased privacy and security, improved efficiency, and greater control for individuals over their digital identities. While the adoption of distributed identity systems is still in its infancy, the potential for growth and innovation in this area is vast, and many believe it could revolutionize the way we manage our digital identities online.
🔑 Key Takeaway
Distributed digital identities (DDIs) herald a paradigm shift in digital identity management, propelling a decentralized, secure, and user-centric approach. While their adoption confronts challenges associated with regulatory compliance, technical complexity, and user awareness, the transformative potential of DDIs to revolutionize the way we interact online is undeniable.