Rise of Maximum Extractable Value (MEV): How Miners Make Profit

7 mins
Last Edited: Oct 06, 2023
Share
Rise of Maximum Extractable Value (MEV): How Miners Make Profit
Comprehensive Guide to Maximum Extractable Value - Learn what MEV is, how it works, key players involved in the process, and types of MEV attacks
Blockchain Infra
Advanced
Have you wondered why MEV attacks have become a critical issue in a blockchain network?
In April 2023, Ethereum MEV bot was attacked, reportedly by one of the blockchain's validators, causing a loss of over $20 million. Moreover, Bank of International Settlements (BIS) has estimated that somewhere between $550 - $650 million of total MEV has been extracted since 2020.*
Let's understand the concept of Maximum Extractable Value/ Miner Extractable Value (MEV) in detailed manner-
What is the Maximum Extractable Value (MEV)?
MEV is the acronym for Maximum Extractable Value or Miner Extractable Value. MEV occurs when the miners can make money by rearranging, adding, or leaving out transactions in a block. Simply put, these block producers can decide which transactions go first on the blockchain and use that control to benefit themselves at the expense of users.
History of MEV
2014
The concept of Miner Extractable Value (MEV) was initially discussed in 2014 on Reddit when an algorithmic user under the pseudonym Pmcgoohan speculated that miners might have the ability to manipulate transactions within the mempool to gain a profit. Pmcgoohan raised concerns about the transparency of miners being able to see and potentially reorder transactions, raising the possibility of front-running and other forms of manipulation.
2019
However, the term "MEV" gained widespread recognition in a 2019 research paper titled "Flash Boys 2.0," authored by Phil Daian and a team of smart contract researchers. In this paper, MEV was formally introduced as "miner extractable value," referring to the total amount of digital assets (ETH in Ethereum's case) that miners could extract by manipulating the order and including transactions within a given time frame. At that time, MEV was primarily discussed in the context of proof-of-work (PoW) consensus mechanisms, where miners held significant control over transaction processing.
2022
When Ethereum transitioned from a PoW to a proof-of-stake (PoS) consensus mechanism during The Merge in 2022, the term "MEV" evolved to "Maximal Extractable Value" to encompass a broader range of methods that miners and validators could use to max their profits.
How does MEV Work?
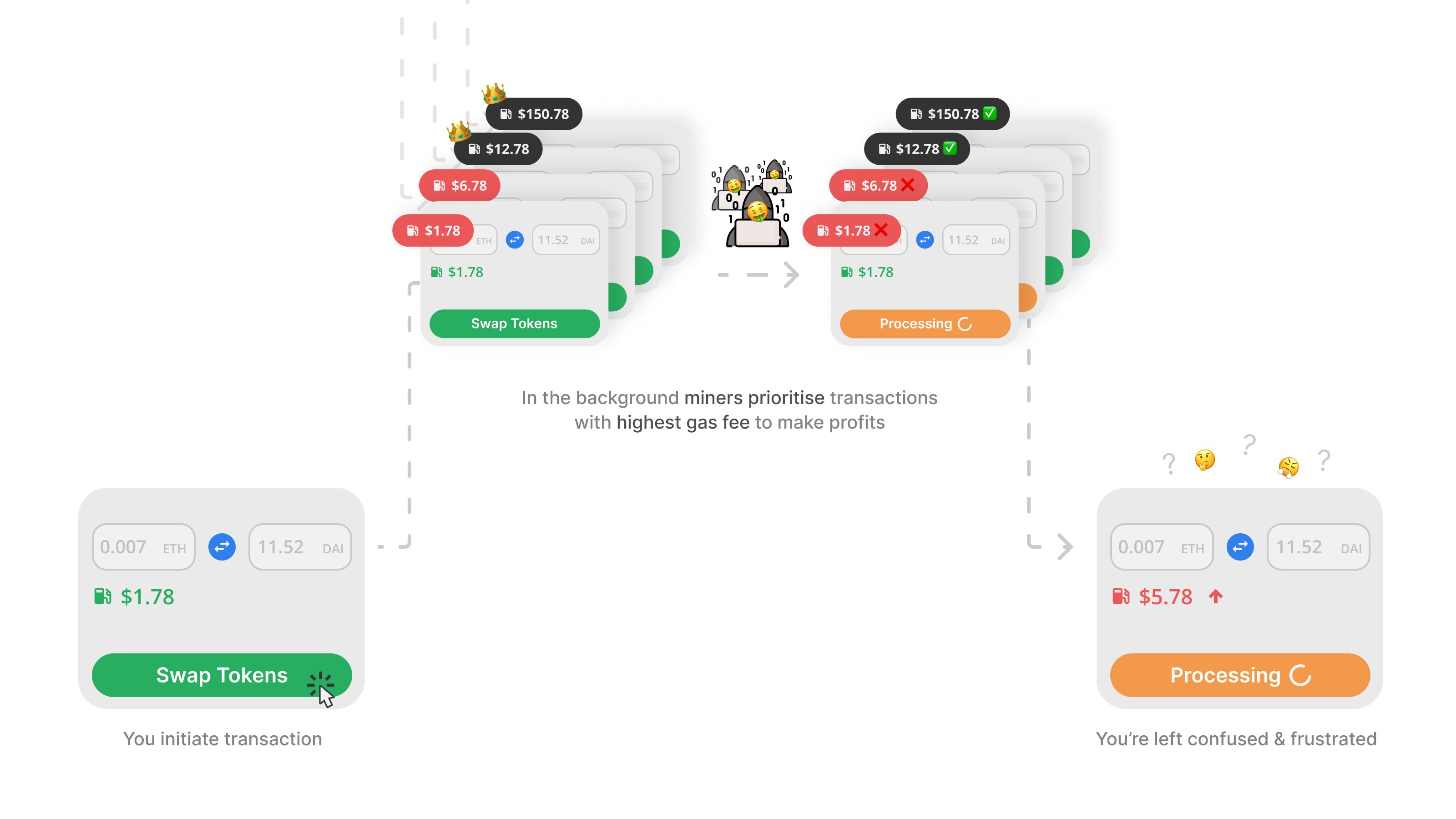
"Blocks recorded in a blockchain are immutable. Once the information is stored, it cannot be changed. However, before a transaction is approved, validators can include, remove, or reorder it in a future block. Every unconfirmed transaction is first routed to the public mempool. Validators then choose which transactions from the mempool to include in the block. Consequently, transactions are chosen based on profitability, meaning those with high gas fees are chosen first. This is why, during peak periods, users pay higher gas fees (or transaction fees) to ensure their transactions are prioritized."
Validators benefit more if they select transactions with the highest fees. As a result, lower-fee transactions have to wait longer to be included in a block. In this way, the validators make the most profitable combination from the user transactions for themselves.
A significant portion of MEV is extracted by searchers and their automated tools rather than validators. When a searcher spots a chance to make a profit, they bundle together a group of transactions. Validators then approve these transactions to extract MEV.
Let's consider a hypothetical example and understand MEV concept in a more simplified manner-
Imagine you want to exchange 50,000 US dollars (USD) for 500 ETH on a decentralized exchange (DEX) with a USD/ETH liquidity pool. Here's what happens:
Mempool runs an automated bot on the Ethereum network that closely watches unconfirmed transactions. These bots collect data from various DeFi applications, including their liquidity volume, price, etc.
When the bots detect that a user intends to buy ETH by submitting a transaction to the DEX, they intervene and manipulate the situation.
Bot decides to increase the price of ETH just before your transaction gets executed. To achieve this, bots add a significant amount of USD to the USD/ETH liquidity pool, which reduces the total ETH the user will receive for their USD.
Due to the bot's actions, your expected exchange rate of $100 per ETH changes instantaneously. Let's say it increases to $120 per ETH due to the bot's intervention.
Eventually, the user's transaction is executed, but not at the rate they initially expected. Instead of receiving 500 ETH for their $50,000, they ended up with only 416.67 ETH due to the altered exchange rate.
The entity behind the bot, typically a validator or a specialized MEV extractor, earns the difference between the original exchange rate and the manipulated rate. In this case, they profit from the 83.33 ETH difference (500 ETH - 416.67 ETH at $120 per ETH) minus any commission or transaction costs associated with their MEV strategy.
Key Players in the MEV Process
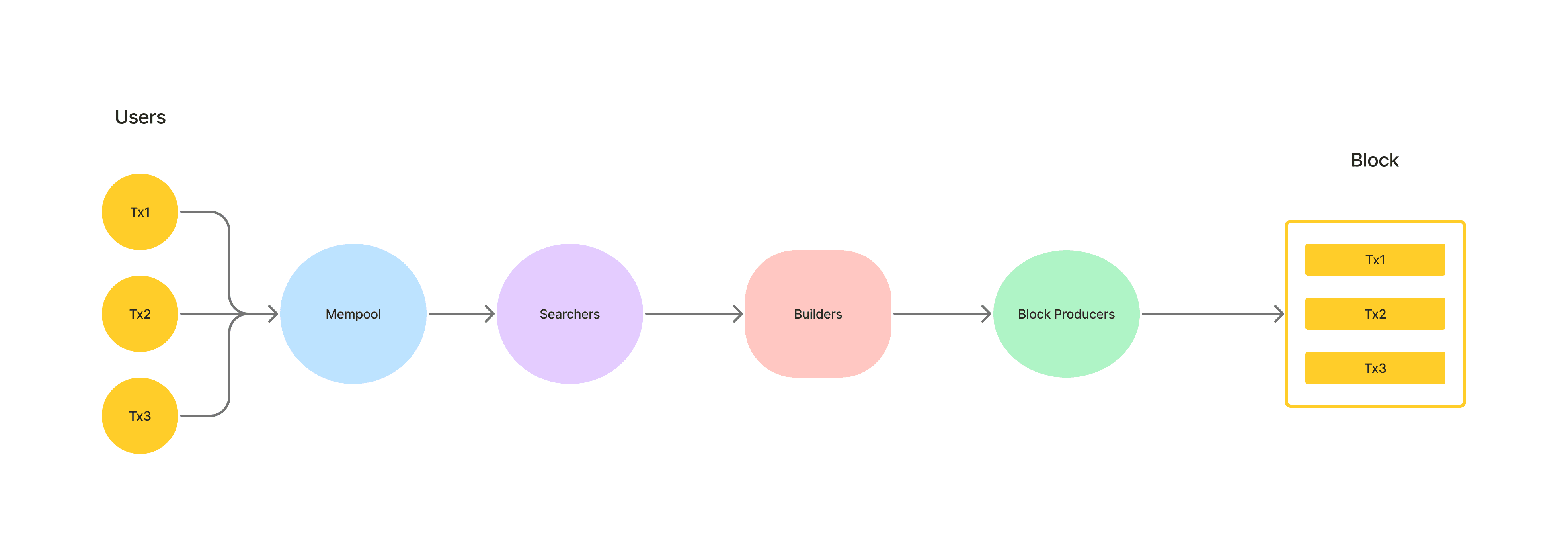
Users
Users are the individuals who initiate transactions from big institutions to everyday retail users. These users set the stage for MEV opportunities with their transactions and orders. By default, these users send their transactions into the public memory pool, where all the action unfolds.
dApps
dApps serve as the bridge between users and the blockchain. They provide users with the means to interact with the blockchain. Users can send transactions through a private relay.
Example: Uniswap , Aave
Searchers
Searchers identify MEV opportunities in the mempool and generate transactions that extract value from those opportunities.Searchers are always looking for MEV opportunities and employ various strategies.
They actively participate in the MEV process by often engaging in a bidding war with outrageous gas prices in on-chain Priority Gas Auctions (PGAs). This bidding frenzy aims to influence how transactions are ordered within blocks by block producers.
Additionally, they use MEV extraction tools like Flashbots to communicate their transaction sequencing preferences to block producers off-chain. It's a way of orchestrating the order of transactions to their advantage.
Example: bloXroute , Flashbots
Builders
Builders are individuals or organizations who assemble blocks by selecting transactions from the mempool and ordering them to maximize MEV. Example: Eden , Flexpool
Block Producers
In the MEV process, block producers can seize opportunities in several ways. First, they can sell precious block space to non-miner MEV extractors. This is often done through Priority Gas Auctions (PGA), and it involves charging high gas fees in exchange for access to the limited space within a block.
Alternatively, block producers can opt to capture MEV for themselves directly. They do this by re-sequencing transactions, which can involve adding, removing, or altering the order of transactions to benefit their interests.
Most Common MEV Attacks
The most common types of MEV attacks are mentioned below-
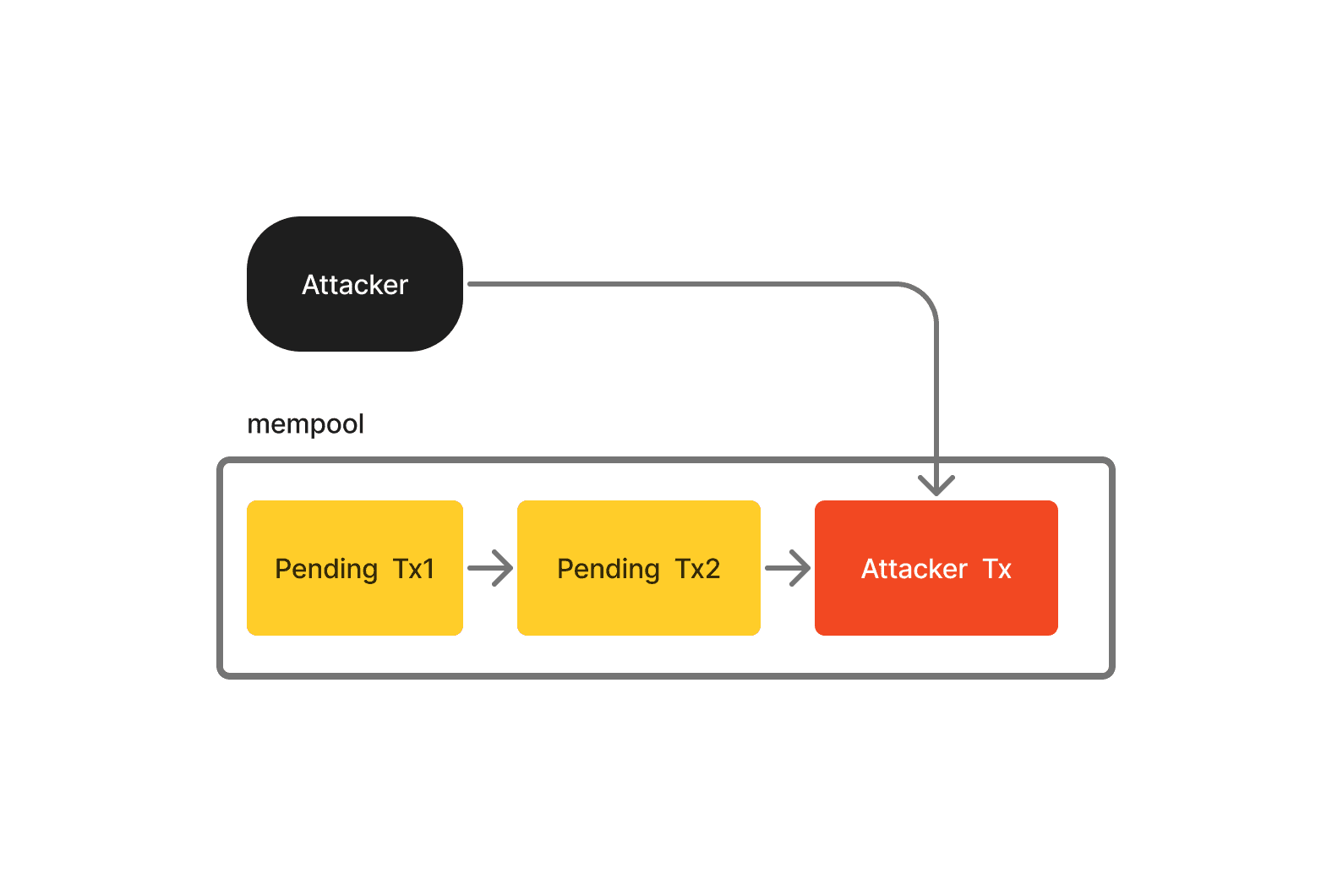
Front-Running
Here, Hacker jumps ahead of a known pending transaction in the queue. They do this with the help of specialized front-running bots that monitor DEX for large orders. These bots then submit their own transactions with higher gas fees, ensuring they get processed before the user's transaction. Front-running is largely used for DEX arbitrage, where arbitrage bots purchase tokens on one DEX at a lower price and sell it on another exchange at a higher price.
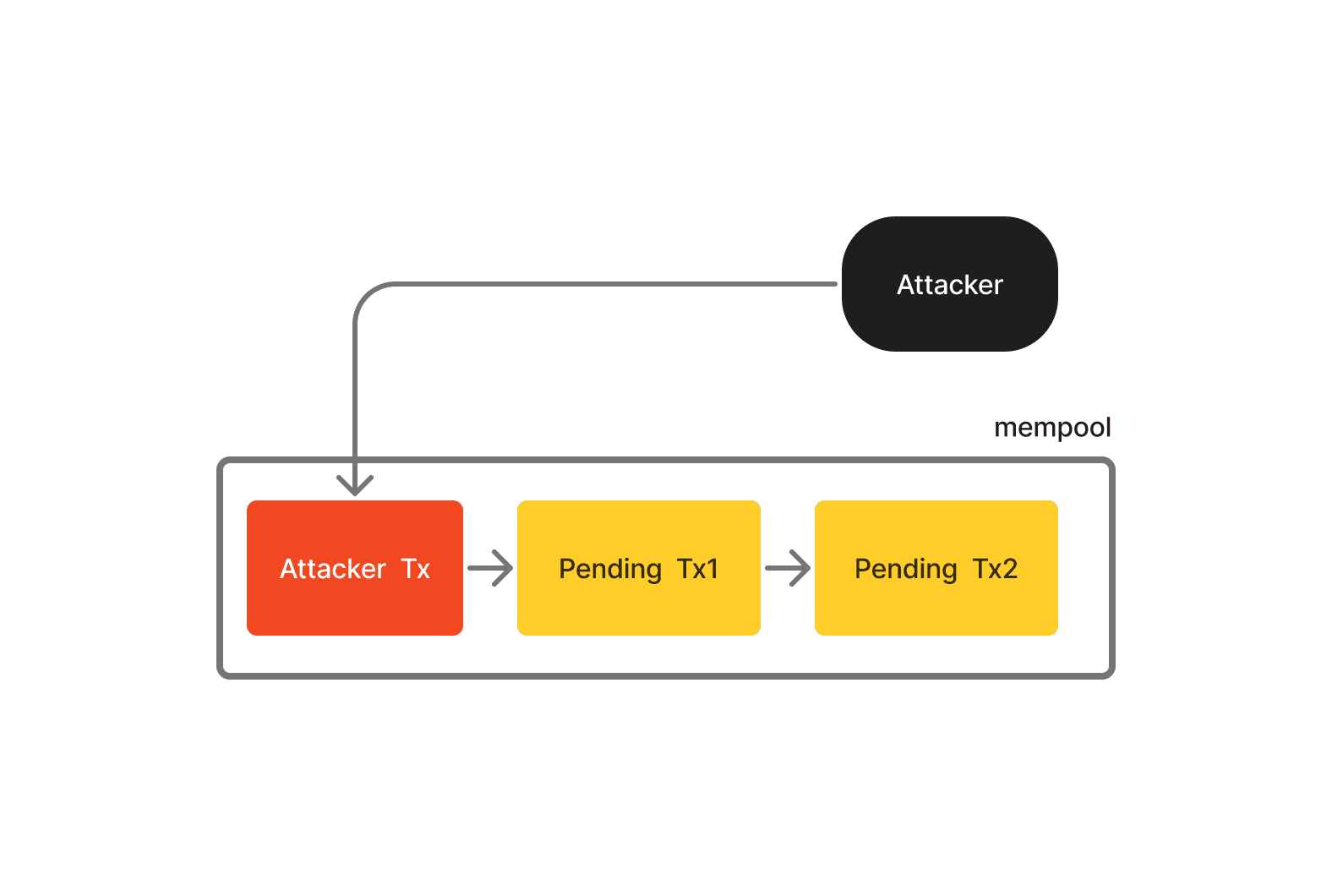
Back-Running
Back-running occurs when a validator places their transaction right after a known pending target transaction. To do this, searchers employ back-running bots, which keep an eye on the mempool for new token pair listings or liquidity pool creations on DEXs.
When these bots spot a new token pair listing, they swiftly place a transaction order just after the initial liquidity setup. They aim to purchase as many tokens as possible, leaving only a small quantity for other users. Subsequently, the bot waits for the token's price to rise after other users buy what's left and then sells the tokens at a higher price to make a profit.
Sandwich Trades
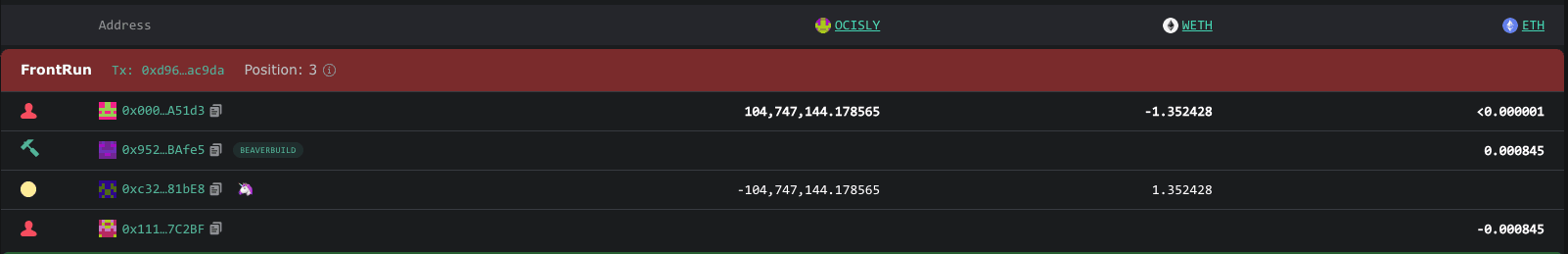
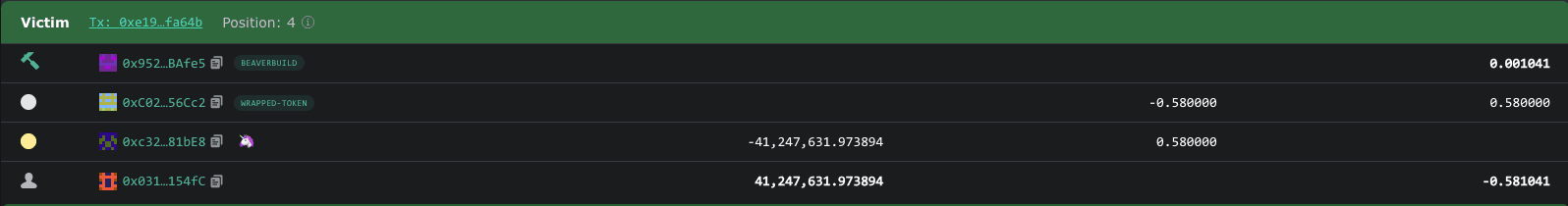
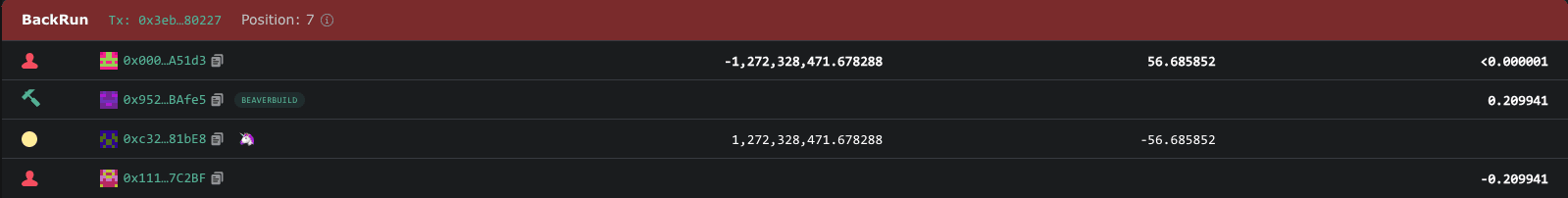
A sandwich attack is a combination front-running and back-running where a validator strategically places two transactions around a pending user's transaction - one before and one after. This tactic commonly extracts MEV from unsuspecting users on decentralized exchanges.
The validator's goal is to manipulate the price of a specific asset. They achieve this by identifying a token that the user intends to buy. Then, they execute a trade to push the token's price higher. After that user's buy order further raises the token's price, the validator sells the token and makes a profit at a high price.
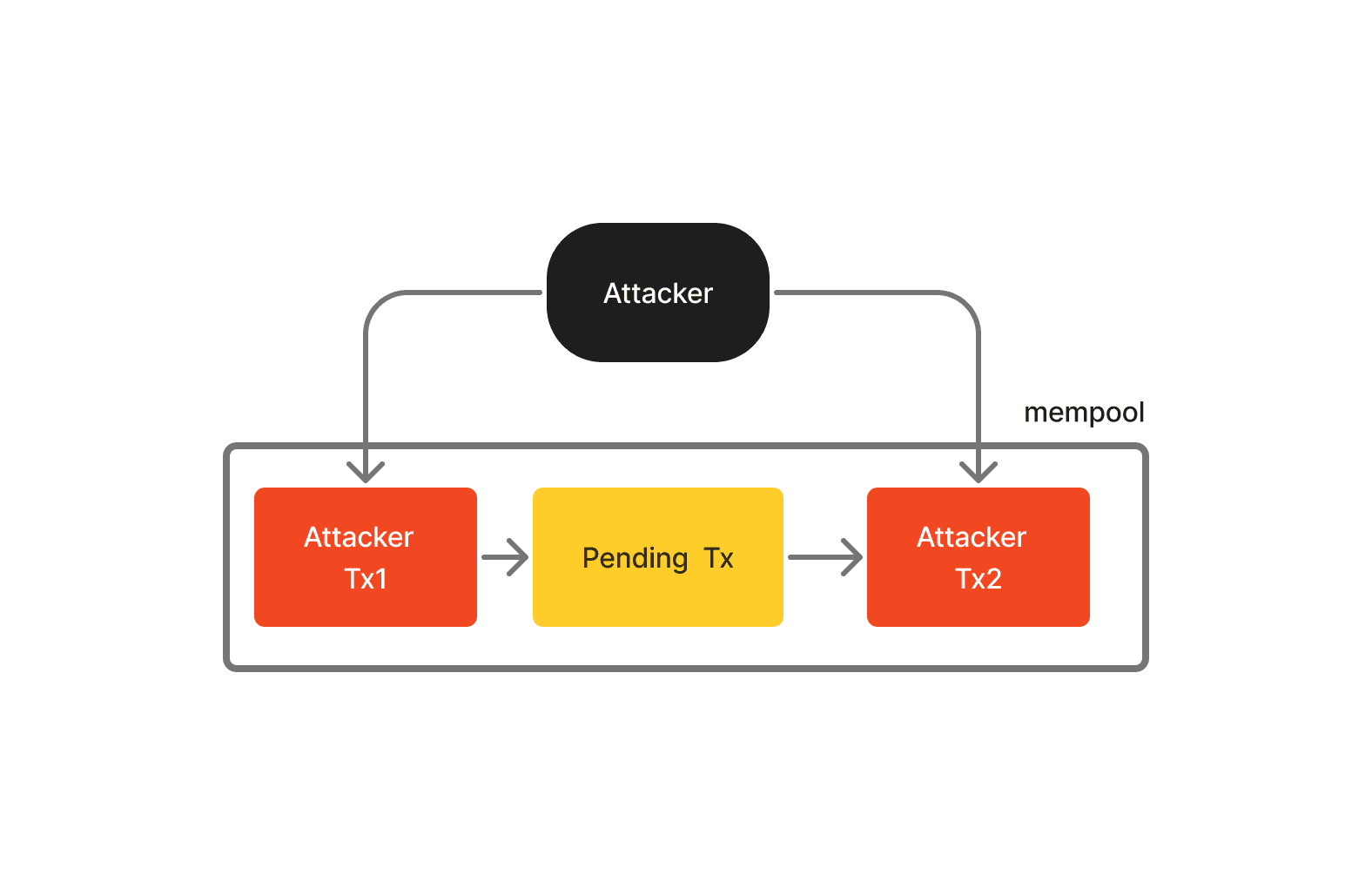
Example:
In this transaction, the attacker launched a sandwich attack, where users were trying to swap from OCISLY token to WETH and made a profit of $65,217
Loan Liquidation
Liquidation aims to extract MEV by focusing on collateralized loans within decentralized on-chain protocols. To execute these liquidations, searchers use automated bots to monitor the network continuously. These bots actively seek out transactions that present opportunities for liquidation. The liquidators then take swift action, either front-running or back-running these transactions, to be the first to liquidate a loan. Their method involves extracting MEV from borrowers by initiating the liquidation before the borrowers can repay their debt. Subsequently, the liquidators profit by selling off the collateral the borrowers had put up as security.
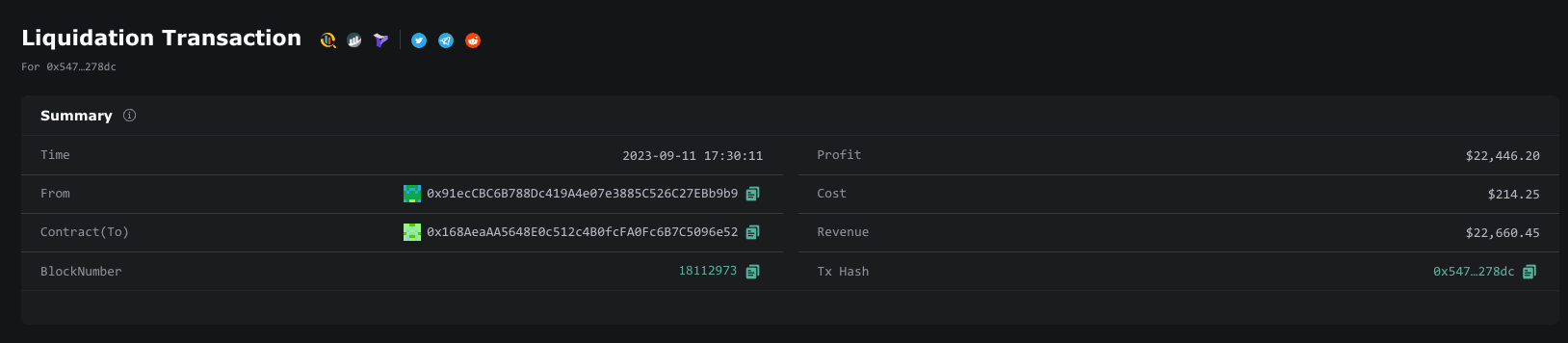
Example:
In this transaction, the attacker used flash loans and made a profit of $22,446.20
NFT Snipping
When new NFTs are minted, people usually use regular Ethereum transactions to buy them. Searchers looking to make the most of the priority game in these NFT drops usually use traditional MEV extraction techniques - gas fee bidding, to gain priority in block ordering and secure a minted NFT. But these searchers go way ahead. They leverage platforms like Flashbots to incentivize validators. Their objective is to bundle multiple NFT purchases within a single block. Once the block is successfully mined, the NFT creator cannot adjust floor prices or delist NFTs. This occurs even if the searcher has acquired every NFT in the drop at its initial floor prices. This type of extraction was first seen in full when an entire line of CryptoPunk NFTs was sniped by a single buyer with the help of a validator.
Example:
One prominent NFT MEV attack occurred when a searcher spent $7 million buying every Cryptopunk at the price floor.
Effects of MEV
There are several repercussions of the MEV attacks -
MEV significantly impacts the effectiveness and fairness of the market within blockchain networks by distorting the system of natural price discovery. It creates market inefficiencies, resulting in higher transaction costs and decreased trust in the ecosystem.
MEV tactics like front-running and back-running may exacerbate volatility in the markets.
MEV can give rise to "dark pools," controlled mempools operated by block producers that directly share MEV profits with users, giving rise to concerns regarding centralization.
The surge in gas prices also impacts regular users, who must either match high fees or risk experiencing delays in their transactions.
Priority gas auctions (PGAs) further exacerbate the situation. Bots engaged in this practice send the same transaction multiple times, resulting in an increased volume of transactions and causing node operators to invest in higher bandwidth capacity to run nodes.
Conclusion
In conclusion, while MEV attacks have presented significant challenges in blockchain, it's important to recognize that the blockchain community is actively working to address these issues. MEV mitigation strategies are continually evolving, driven by the collaborative efforts of developers, researchers, and the wider crypto ecosystem. From smarter contract design to innovative protocols like Flashbots and even fundamental changes in consensus algorithms, the landscape of MEV solutions is dynamic and adaptive.
The next article explores the solutions and the prospective strategies for countering MEV attacks.
Reference links
https://explore.flashbots.net/ https://docs.flashbots.net/ https://collective.flashbots.net/
🔑 Key Takeaway
MEV attacks in blockchain networks have grown significantly, impacting users, market fairness, and decentralization. Solutions like Flashbots and Proposer-Builder Separation are emerging to address these challenges, offering a more secure and equitable blockchain ecosystem.